In a result of its research investigation efforts, Security Explorations, a research lab of AG Security Research company, discovered multiple security vulnerabilities in Telit Cinterion IoT modem gateways.
This section of our website presents initial information regarding the project.
Telit Cinterion IoT description (and vendors' claims / statements)
Telit Cinterion products brand consist of cellular wireless communication modules, gateways and data (modem) cards, ranging from 4G LTE, LPWAN to 5G. They target automotive, medical, energy and telecom industries.
Cinterion product portfolio was acquired by Telit from Thales company in 2022. Starting from Jan 2023, Telit Cinterion was responsible for handling all security matters pertaining to the acquired product line.
Prior to the acquisition, the following claims were made by the original vendor (Thales) about security posture of IoT gateways that included Cinterion modules:
- "Strong gateway cybersecurity is critical to IoT ecosystem trust"
- "Thales IoT Gateways are the only industrial IoT gateways to safeguard the complete data-to-cloud journey for the device's lifetime" (source)
The following statement was made by Telit at the time of announcing Cinterion portfolio acquisition:
- "Telit Cinterion will leverage Thales' expertise in IoT security across SIM technology, modules, and connectivity"
- "This transaction with Thales is arguably the most impactful one for Telit competitiveness...it will also enable us to deliver all new offerings derived from the experience, expertise, and the DNA of two companies that have made security and quality part of their brand promise from the very beginning" (source)
Demonstration movies
- "Local compromise and information extraction from DGL61-W device", MP4 movie file, 42MB
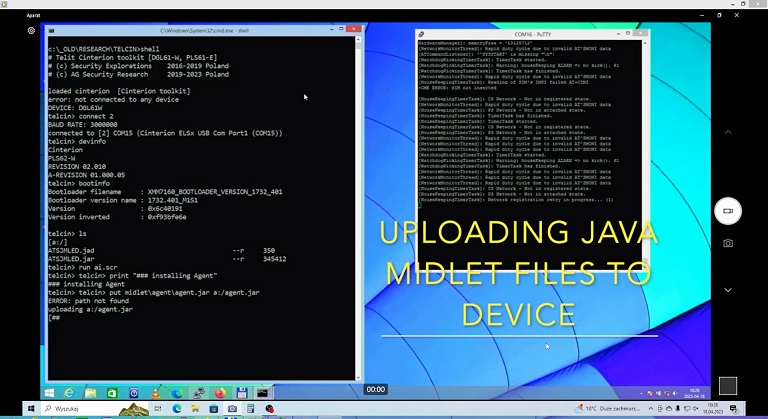
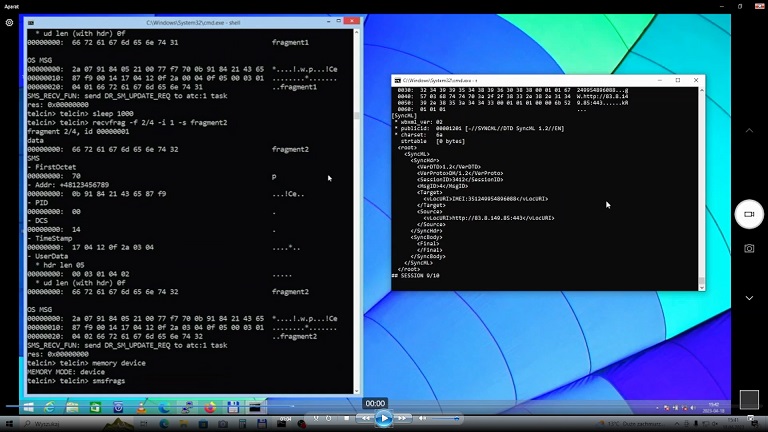
- "Remote code execution through SMS fragmentation issue on DGL61-W device", MP4 movie file, 35MB
Notes
Telit company has been notified and provided with full access to research material for evaluation purposes (communication from Jan 11, 2023, all key vulnerabilities were reported to the company in Jan 2023).
In Feb / Mar 2023, as a result of a signal of ongoing analysis of OMA DM and SMS handling issues at Telit end still taking place 1.5 month following the reporting and regardless of a comprehensive material provided, additional work was conducted free of any charge and information submitted to the company of which goal was to help it evaluate the impact of a remote SMS handling issue (demonstration of a viable attack scenario). Support was also provided to the company free of any charge in order to solve the problems with PoC compilation and execution.
On Apr 17, 2023, the company provided the results of its triage regarding the reported issues.
Telit informed that the base device for which all of the issues got reported (DGL61-W) is at the end of its lifecycle and EOL was announced to customers.
The company also indicated that IMEI number leak (Issues 16) is an intentional feature and part of the OMA DM protocol and that it doesn't consider it a vulnerability on its own.
Issues related to privileges granted by default to Java applications and facilitating hijack of system AT commands (Issues 4 and 17) were not considered vulnerabilities on their own (described as intentional features and by design rely on customer properly configuring the security of the embedded processing capability). This evaluation is questionable as system commands hijacking by 3rd party code undermines trust to the operating system environment, such a hijacking may also lead to the development of a stealth / persistent backdoor (i.e. AT^SFSA command may return false information about the state of a file system).
The remaining issues (which include remote ones) were evaluated with a final risk as not critical - the company made its evaluation upon the use cases and configurations of its major customers.
Affected platforms
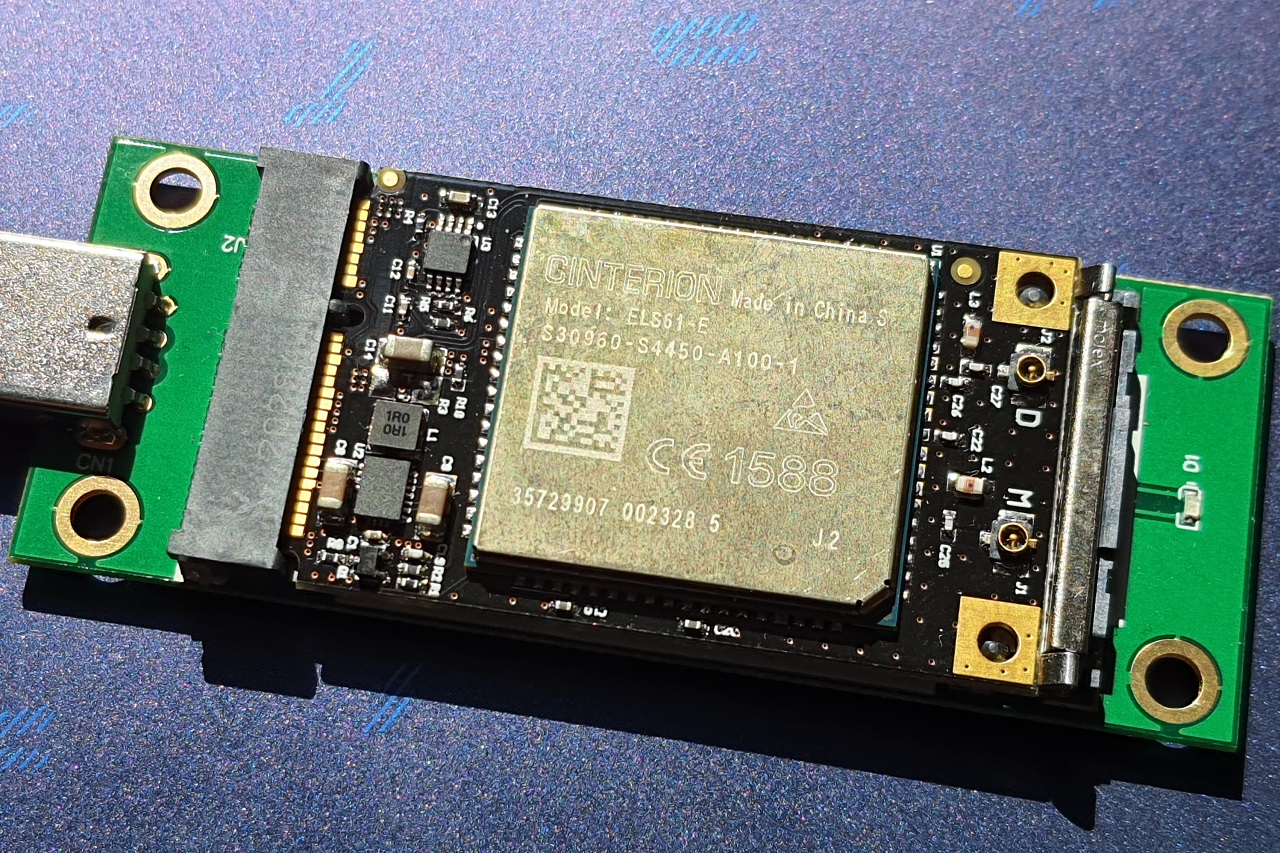
The core research has been conducted with respect to DGL61-W modem gateway. Complete, local device compromise has been also confirmed on ELS61-E miniPCIe module illustrated on a picture below. Default device configuration was used in both cases.
On Apr 20, 2023 Telit completed previous insufficient information about impacted devices and their SW versions with the following information.
Vulnerabilities impacting only DGL61-W (Issues 8-11). The DGL61-W incorporates the PLS62-W module with pre-installed ATSJMLED Java MIDlet.
- ATSJMLED MIDlet - all versions lower than 0.1.59
Vulnerabilities impacting products with OMA DM client (Issues 12-15, 18). Following products are impacted (variants for US market):
- ELS61-US/-USA: all FW versions
- PLS62-W: all FW versions
- ELS81-US: all FW versions
Vulnerabilities common for the platform baseline (Issues 1-3, 5-7). Following products are impacted:
- BGS5: all product variants and FW versions
- EHS5/6/8: all product variants and FW versions
- PDS5/6/8: all product variants and FW versions
- ELS61/81: all product variants and FW versions
- PLS62: all product variants and FW versions
Fixing status
Telit informed that the company rolled out a vulnerability fix for the most critical issues and it is going to suggest some mitigation actions to its customers for the other findings.
The company also indicated that a new version of ATSJMLED midlet has been already released (fix for Issues 8-11). The build date of the files, indicates Jan 18, 2023 (a fix without prior notification / coordination). There has been no information on the web page where the fixed app version has been made available about the security nature of the new release (a silent fix).
The only information received from Telit regarding fixes took place on Feb 27, 2023 when the company informed that "a fix is planned" for some of the issues (these were not described) and it would keep us updated. No update was provided by Telit prior to the rollout of the fixes though (we learned about the fixes from Apr 17, 2023 "triage" message).
Missing impact / vulnerabiity origin information
Both, DGL61-W and ELS61-E devices rely on Intel modem chipset (XMM7160). They embed Intel specific code for OMA DM client too. It is not clear though if remote issues such as OMA DM auth bypass have its origin in Intel code or were introduced by the previous Cinterion vendor (Thales). In that context it is not clear if Intel should be forwarded and handle vulnerability information (root cause in Intel provided code implicates potential impact to other 3rd parties / licensees)
Similarly, it is not clear if Java path issues (likely having its origin in J2ME classes and file protocol handler) have its origin in Oracle code for embedded J2ME or vendor specific customizations.
When inquired about the abovementioned vulnerabilities origin (whether in Intel / Oracle code), Telit informed that the company cannot comment on code provided by its platform supplier as it is covered by NDA.
Telit Product Security Incident Response Team (PSIRT) web pages state that PSIRT reserves the right to forward details of issues reported to it if they affect third-party components or external projects. Throughout this process, PSIRT will continue to coordinate and communicate with researchers. No communication regarding forwarding of any issues to any 3rd party company took place. It is not clear if any forwarding took place. Any vulnerability forwarding shouldn't take place without original researcher's (bug discoverer's) consent / approval as:
- the original bug discoverer should hold the right to decide about who its bug is shared with (other 3rd parties should learn about it either directly from a bug finder or from a public release)
- the original bug discoverer might be eligible for a credit in a public security bulletin of a 3rd party company
- the original bug discoverer might be eligible for a Bug Bounty reward of a 3rd party company (such as Intel Bug Bounty Program)
Vulnerabilities impact
Our lab tests conducted with the use of an emulated SMS reception functionality (real life test was avoided as it could leak vulnerability to 3rd parties present in a mobile network operator) indicate that a successful exploitation of a combination of the vulnerabilities make it possible to compromise a vulnerable Cinterion device from a remote network location. Only phone number of a target device would need to be known to accomplish that (the exploitation is triggered and proceeds with the use of SMS messages among others).
As a result of a successful compromise, privileged access to the vulnerable device could be gained. This includes code execution access (with ARM Supervisor level). Such an access could be further leveraged for the following:
- secrets theft
- access to backend services
- bricking the device (making it unusable, by erasing / overwriting firmware)
- backdooring the device (a silent backdoor can be implemented)
- using the device for calls to premium telephone / SMS numbers
- using the device as a massive SMS sender (spam messages, phishing messages, messages pointing to an exploit page)
- using the device as a proxy in attacks (launch attacks against other networks from the device, use of the number as an identity verification, etc.)
- sniffing of some of the communication occurring through the device (if not encrypted)
- providing false information to the cloud server (such as SLAE), proxying communication with cloud server (so that all traffic goes through attacker's server)
It is worth to note that Telit has not been able to fully replicate SMS fragmentation issue (Issue 18), upon code analysis, the company confirmed it should be in theory feasible.
As the company signalled trouble to execute the PoC two months following the reporting, we fear Telit might be lacking proper competences / engineering resources when it comes to evaluation of security issues (PoC execution problem could be solved by using the precompiled binaries delivered to the company as part of the initial research package from Jan 2023).